A 2023 assessment by the North American Electric Reliability Corporation (NERC) emphasized that physical and cyber security attacks on critical infrastructure are increasing. Physical attacks on power grids rose by a staggering 71% in just one year. A notable recent example was the December 2022 shooting attack on two substations in Moore County, North Carolina, USA. This resulted in significant damage and widespread blackouts that affected around 45,000 customers. This incident exposed potential security vulnerabilities in the nation’s power grid and illustrated the potential for severe operational disruptions.
The challenges of securing critical infrastructure
Critical infrastructure encompasses energy, communications, water, and transportation, for which specific examples include power substations, water and gas facilities, and nuclear plants. This infrastructure faces various risks from unauthorized access, equipment tampering, theft, and physical attacks, leading to severe repercussions for public safety, health, and business operations. Each facility faces a unique set of security challenges, which often include;
Perimeter security: Securing the perimeter of a critical infrastructure site may involve protecting gates and fence lines from unauthorized access. Traditional fencing and surveillance methods struggle to cover large areas effectively, leading to security vulnerabilities.
Critical zone protection: Inside critical infrastructure facilities, certain areas such as transformer banks and control rooms are particularly sensitive. Unauthorized access to these zones can lead to catastrophic failures or safety hazards. Areas that are very high-risk, such as nuclear plants, require even more stringent security to meet regulatory compliance.
Remote zone protection: Many critical infrastructure sites are located in remote areas and/or span large distances. Securing and monitoring an extensive network of sites or infrastructure (e.g. water supply access zones or pipelines), requires heavy investment in traditional surveillance and motion sensors. Due to remote locations - it is critical to reduce the false alarms in these sites to ensure interventions are only done when real threats occur.
The limitations of traditional security measures
Traditional security approaches for critical infrastructure often rely on physical barriers, CCTV cameras, and motion detectors. While these methods are essential, they come with several limitations:
Inadequate detection range & accuracy: Although cameras and other sensors are crucial for security monitoring, they often struggle with depth and scale perception, making it challenging to accurately detect and assess the size, distance and speed of moving objects in 2D. This issue is compounded in low-light or adverse weather conditions, leading to security vulnerabilities, false positives and missed events.
High operational costs: Addressing the shortcomings of traditional sensors and security systems often requires substantial investments in additional equipment and security personnel, which increases operational costs. Managing false alarms from low-performing sensors and maintaining equipment further adds to the expense. Consequently, traditional security systems require significant investments to ensure effective protection.
In contrast, lidar (light detection and ranging) technology has emerged as a high-performance, cost-efficient solution for enhancing physical security. Its reliable and accurate detection capabilities make it particularly well-suited for critical infrastructure applications, offering a robust addition to enhance traditional security measures.
The advantages of a lidar detection solution
Digital lidar sensors offer a significant advancement in addressing the limitations of conventional critical infrastructure security systems:
High-resolution 3D mapping: Lidar uses laser pulses to create a detailed 3D view with centimeter-level accuracy of the environment to create an exact digital twin of a critical infrastructure site allowing for precise 3D spatial awareness.
Accurate intrusion detection: Detecting and responding to intrusions in real-time is essential for maintaining security. Lidar technology can accurately detect in 3D hundreds of feet away with high performance under the most challenging conditions such as poor light, fog, rain and snow.
Enhanced tracking: Lidar is able to accurately track moving objects at range, which is crucial for monitoring large areas and protecting critical zones within various types of infrastructure.
Gemini perception software takes digital lidar to the next level
Ouster Gemini, a lidar detection solution, combines Ouster’s digital lidar sensors with Ouster’s perception software to amplify the detection benefits of lidar technology. This provides a robust intrusion detection, which is extremely valuable for securing critical infrastructure:
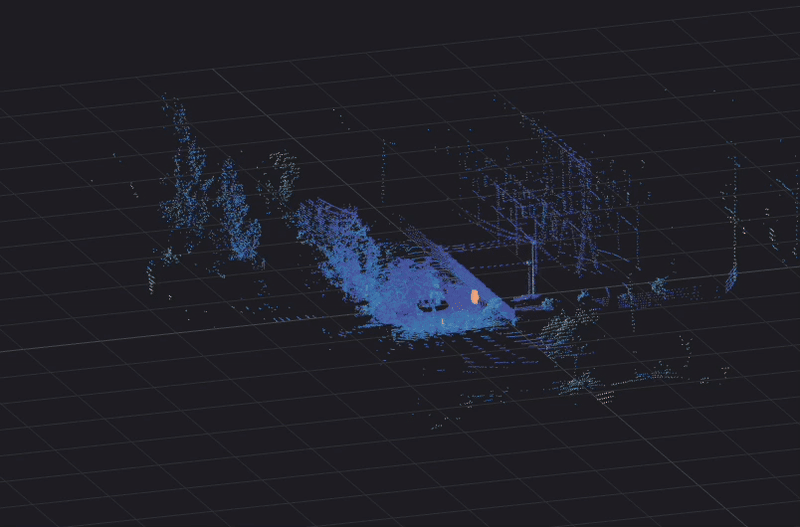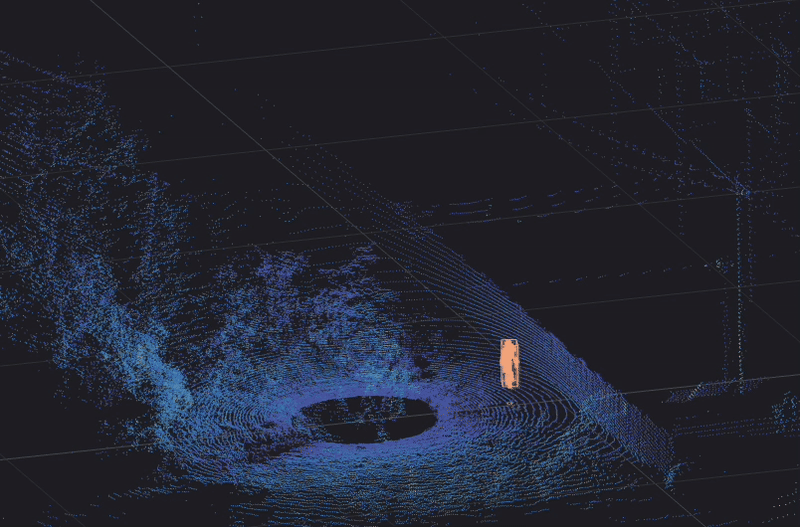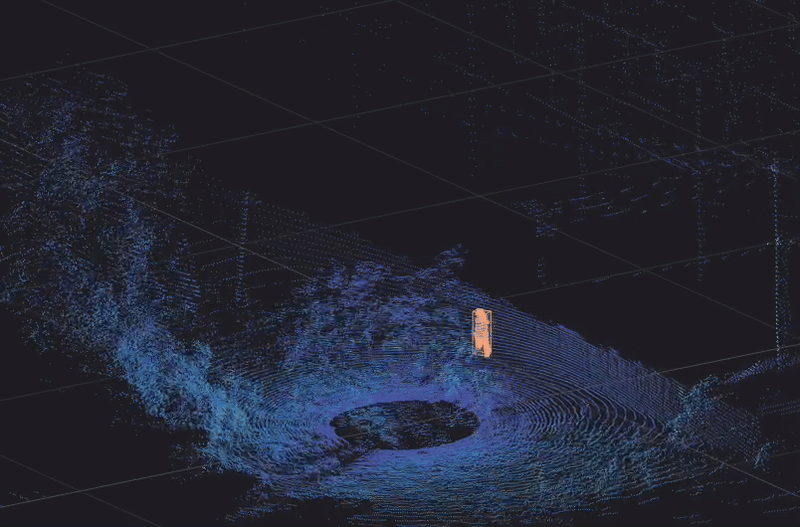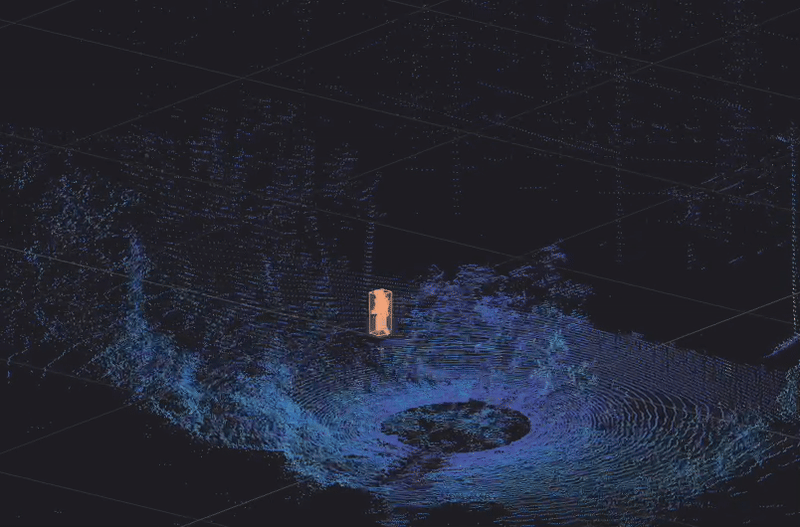
3D mapping creates a digital twin of your entire site: Ouster digital lidar sensors produce up to 5.2 million points per second by processing light returns from each laser beam shot. Point clouds created from multiple meshed Ouster lidars provide a real-time digital twin of an indoor or outdoor site in 3D with unparalleled detail and accuracy.
Example point cloud output from one Ouster OSO digital lidar sensor
A person is detected, classified and tracked in 3D by Ouster Gemini walking along a fence line in a warning zone
- Wide area coverage: One Ouster lidar provides up to 90 meters (~300 ft) of detection with Ouster Gemini. Sites are designed using Ouster’slidar design software. Multiple Ouster lidars can be meshed together for 360° coverage across an entire area.

Example Ouster lidar coverage software used in the design workflow
Real-time detection, classification and tracking: Using heuristic and advanced AI deep learning algorithms, Ouster Gemini detects, classifies, and tracks moving objects, such as people and different types of vehicles. It can distinguish between real threats and false events, reducing false alarms and missed events. Combining 3D views from multiple lidars allows seamless tracking of an intruder across a monitored area using a unique ID.
Customizable zones: Ouster Gemini allows the creation of detailed, unlimited 3D inclusion and exclusion zones of any shape or size within the sensor's field of view. Warning and alarm zones can be created and event recordings saved for post event analysis.
Seamless integration: Ouster Gemini integrates with leading video management systems (VMS) to provide a single pane of glass for security personnel. Following the detection of a real intrusion, Ouster Gemini is able to direct PTZ cameras to slew to the point of an intrusion and track accordingly. Bringing Ouster Gemini 3D detection capabilities directly into the VMS provides enhanced layers of detection, automation and performance in the control room.
Industry standards & certifications: Ouster Gemini is NDAA compliant, and ISO 2700l and Buy-American certified OS sensors for additional assurance.
Practical Applications for Critical Infrastructure Sites
Perimeter security
Protecting extensive infrastructure networks and sites is a major challenge. By implementing Ouster Gemini, critical infrastructure sites can be monitored 24/7 with high reliability. Crawling, walking and running intruders along with all types of vehicles, can be detected, classified, and tracked with a unique tracking ID. Hundreds of unique IDs can be simultaneously tracked, measuring 14 different data types. This includes speed, trajectory, volume, heading and precise location coordinates in real-time and with centimeter-level accuracy.
The ability to detect intruders in any lighting conditions means that perimeters do not need to be lit up, reducing significantly operational costs and carbon emissions.
An intruder crawling is accurately detected, classified and tracked with a unique ID in Ouster Gemini
Tailgating
Tailgating is a prevalent security issue where unauthorized individuals gain access by closely following authorized personnel through secure entry points. Ouster Gemini offers a solution by creating virtual zones around secured entrances. If an unauthorized person or vehicle breaches these virtual boundaries and attempts to tailgate, Ouster Gemini will send an alertand track the intruder so security personnel can intercept at the exact location of the intrusion.
Ouster Gemini for tailgating detection
Red zone monitoring
By setting up 3D virtual monitoring zones in Ouster Gemini, security teams can ensure that any unauthorized access to sensitive areas triggers immediate alerts and recorded events, protecting critical assets and/or areas from intrusion in any lighting and weather conditions
The video showcases a 3D digital twin of a remote infrastructure site in Ouster Gemini. As the intruder approaches the fence line, a warning alert is triggered followed by an alert as they enter the exclusion zone. The intruder is tracked with a unique ID
The future of critical infrastructure security
As security threats continue to evolve for critical infrastructure sites, so must our methods for addressing them. Ouster Gemini sets a new standard for protecting vital facilities and infrastructure, addressing the limitations of traditional security systems and offering a comprehensive solution for safeguarding vital physical infrastructure. What's more, we make evaluation easy and low-risk with the Ouster Geminar Starter Bundle. To learn more, contact our team today.